Solution
We are therefore building the first ultra-secure messaging and social computing platform, around an ultra-secure cloud, and a 2mm-thin personal computer that you and your close associates will carry embedded in stylish custom leather wallets.
We ensure previously unimagined levels of privacy and security - and a transparent in-person solution to the need for legitimate and lawful access - via an uncompromising zero-trust approach down to CPU design, chip fabrication oversight, and data room access, as validated by a highly democratic and resilient Trustless Computing Certification Body, being promoted by our non-profit arm.
Initially reserved for clients and executive staff of private banks, family offices, UHNWIs and enterprises, it seamlessly enables ultra-secure messaging, social networking, transactions, and dozens of 3rd-party apps. You can communicate and network with freedom and peace of mind with your close family, personal, business associates, as well as sign contracts, and engage in e-banking, and more with dozens of third-party apps.



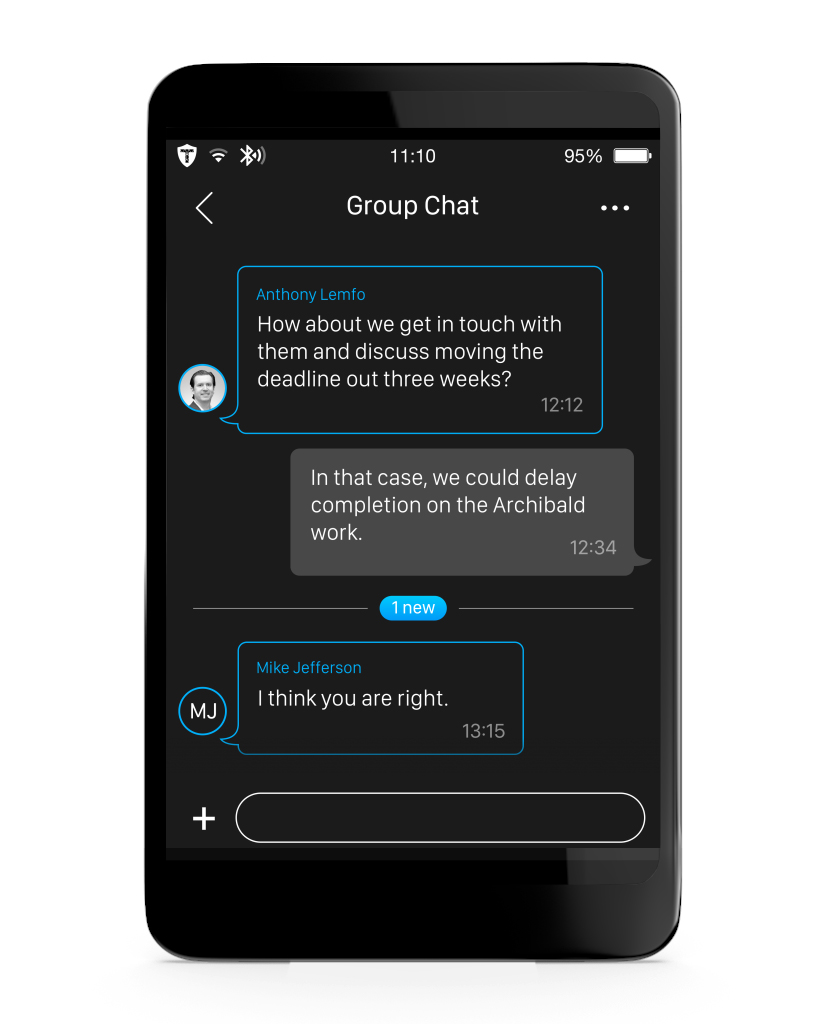



















![[Confidentail Name]](https://images.squarespace-cdn.com/content/v1/59b8e1bb18b27d9734d7b147/1605027667997-495182LNVLVX4BF6IJ93/image-asset.png)


![[Confidential Name]](https://images.squarespace-cdn.com/content/v1/59b8e1bb18b27d9734d7b147/1605027764519-BUAN4HQX2CE3561BQ5J5/image-asset.png)








